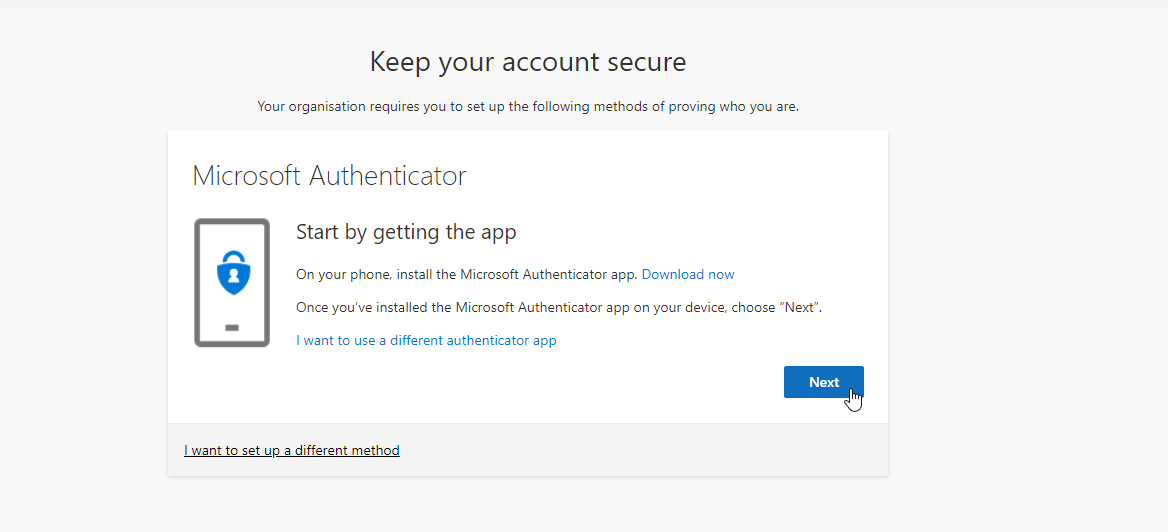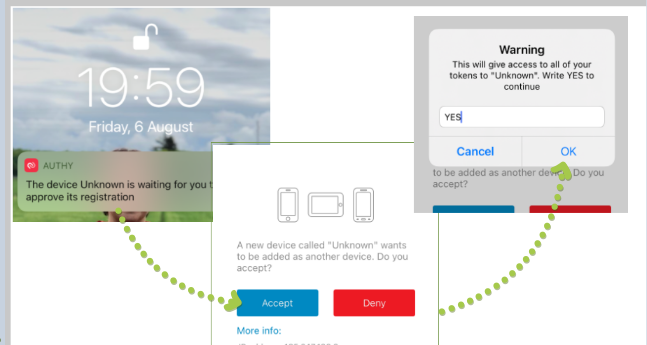
Token2 | Strong authentication with hardware tokens OATH-TOTP SHA-1 SHA-256 | How to transfer TOTP profiles from Authy to a Token2 hardware token | TOKEN2 MFA Products and Services | programmable hardware
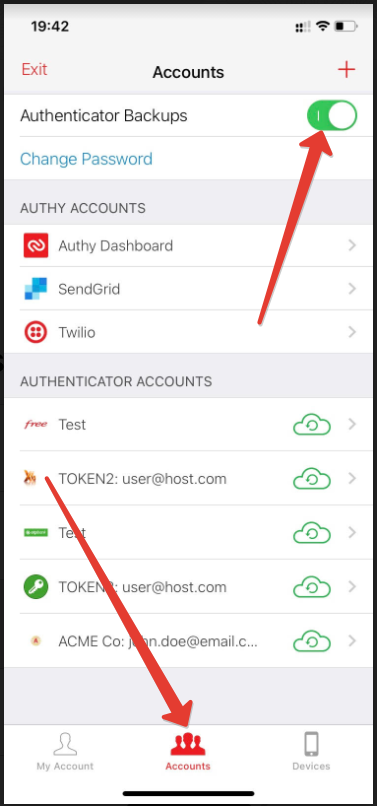
Token2 | Strong authentication with hardware tokens OATH-TOTP SHA-1 SHA-256 | How to transfer TOTP profiles from Authy to a Token2 hardware token | TOKEN2 MFA Products and Services | programmable hardware

Token2 | Strong authentication with hardware tokens OATH-TOTP SHA-1 SHA-256 | How to transfer TOTP profiles from Authy to a Token2 hardware token | TOKEN2 MFA Products and Services | programmable hardware




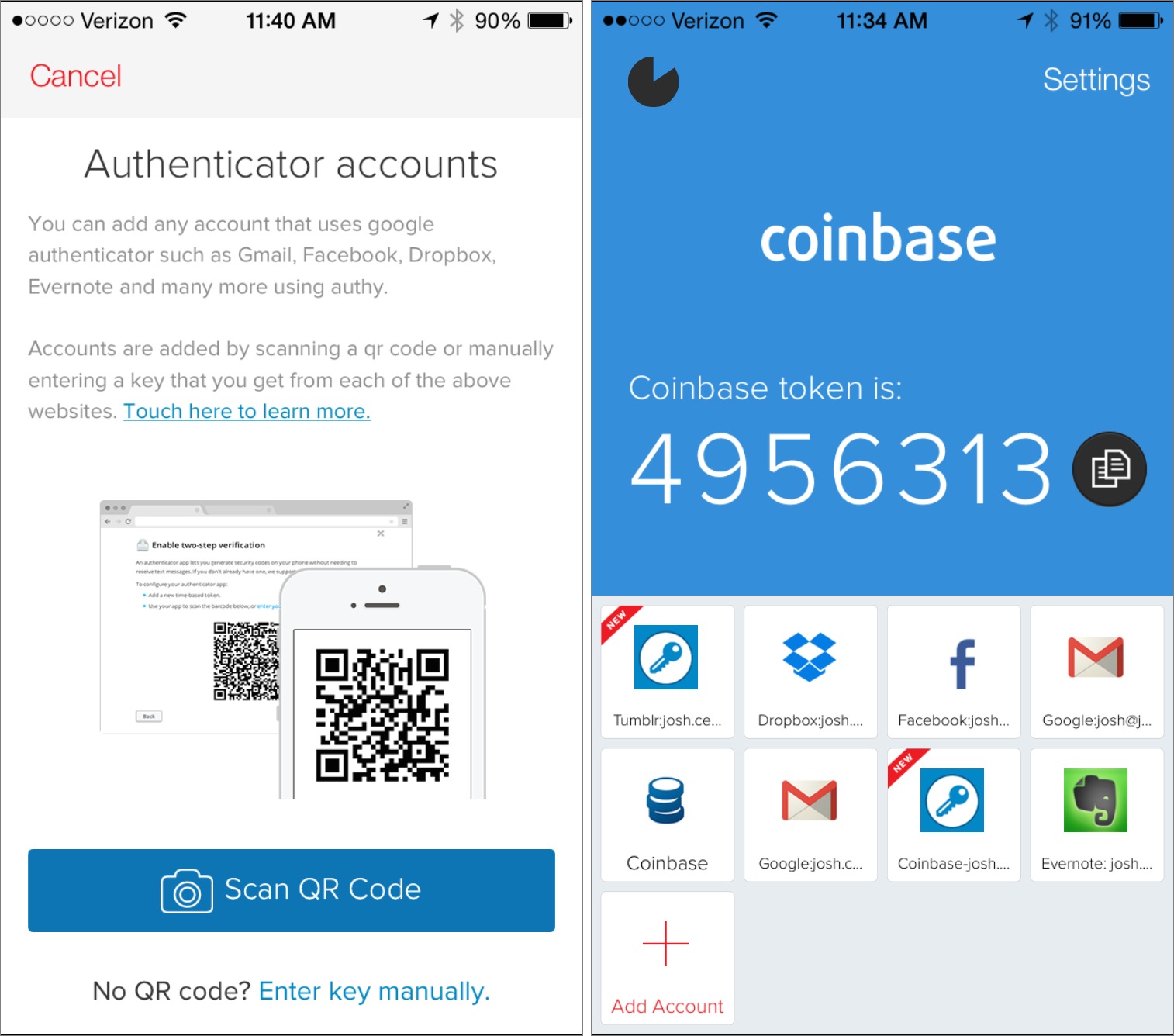




![FEITIAN OTP c200 NFC Enabled OATH Time-based [TOTP] 2FA Token | I34 – FEITIAN Technologies US FEITIAN OTP c200 NFC Enabled OATH Time-based [TOTP] 2FA Token | I34 – FEITIAN Technologies US](http://cdn.shopify.com/s/files/1/0053/2889/6034/products/I34Front_f429f682-4f0e-491b-9528-adb791c34eb3.png?v=1622140961)