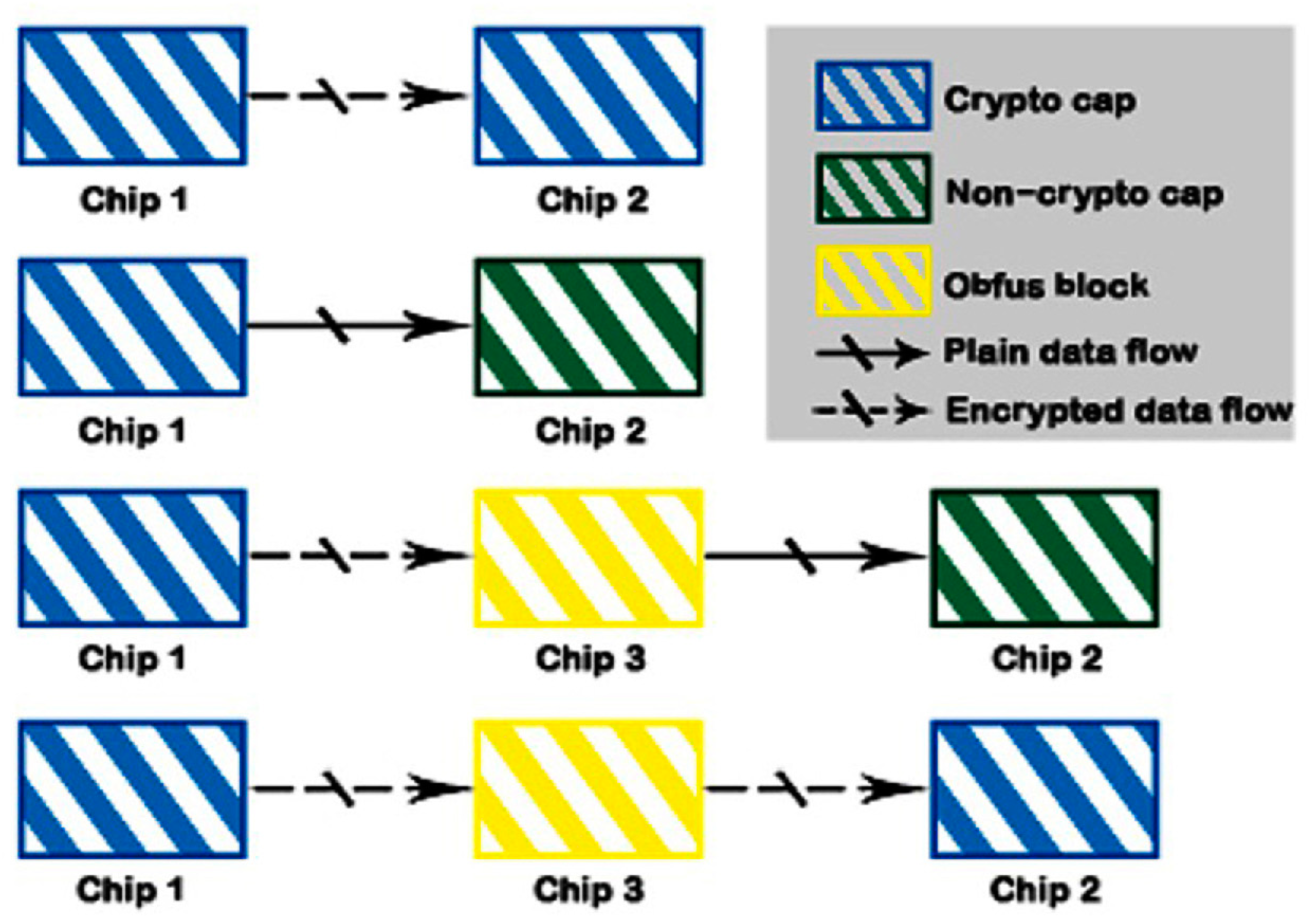
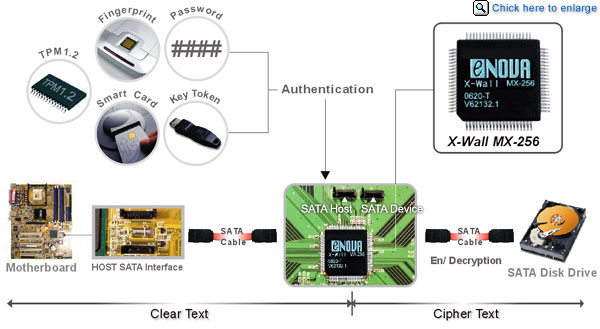
Smart Card less system architecture with encryption hardware within the... | Download Scientific Diagram

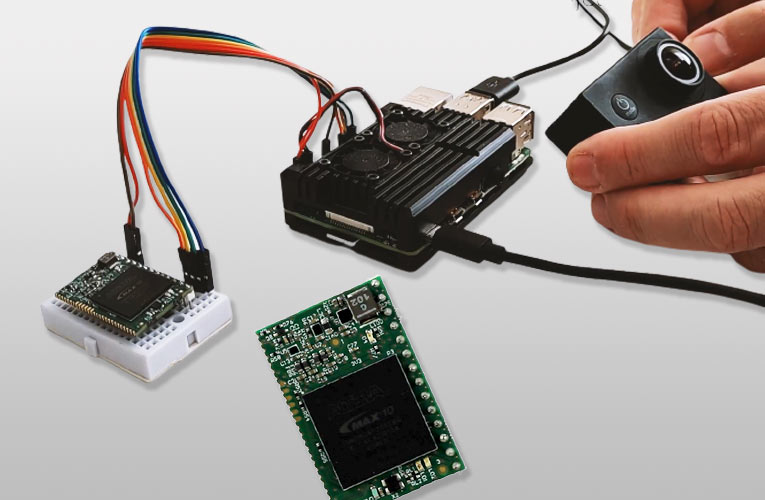
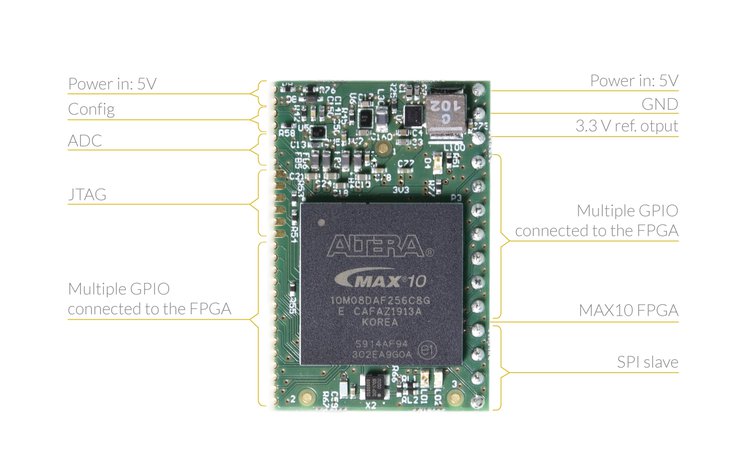
Kryptor FGPA is a Hardware Security Module that adds Complex Open-source Encryption - Electronics-Lab.com

Information | Free Full-Text | FPGA-Based Voice Encryption Equipment under the Analog Voice Communication Channel

Integral 64GB Courier-197 256-Bit USB Stick verschlüsselt - USB Stick Passwort geschützt - FIPS 197 zertifiziert, Schutz vor Brute-Force-Angriffen & Super USB3.0 Übertragungsgeschwindigkeiten: Amazon.de: Computer & Zubehör

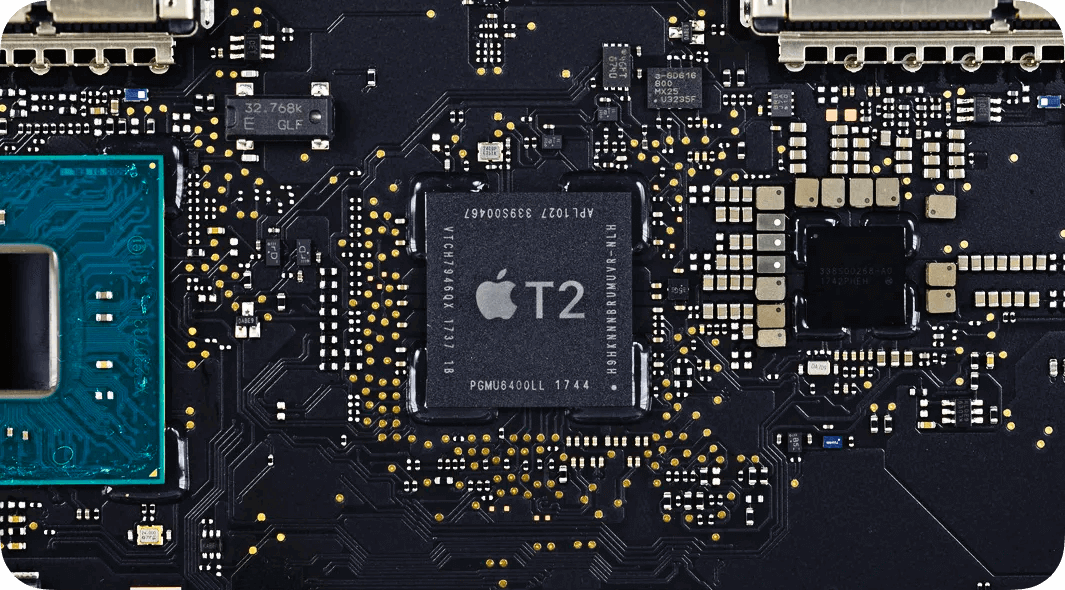
Cabel on Twitter: "⑤ Security. This new chip means storage encryption keys pass from the secure enclave to the hardware encryption engine in-chip — your key never leaves the chip. And, they

Pampfort Military Level AES 256-bit Standard Encrypted USB Drive, with Hardware Encryption Chip,Metal Shelled,32GB: Buy Online at Best Price in UAE - Amazon.ae