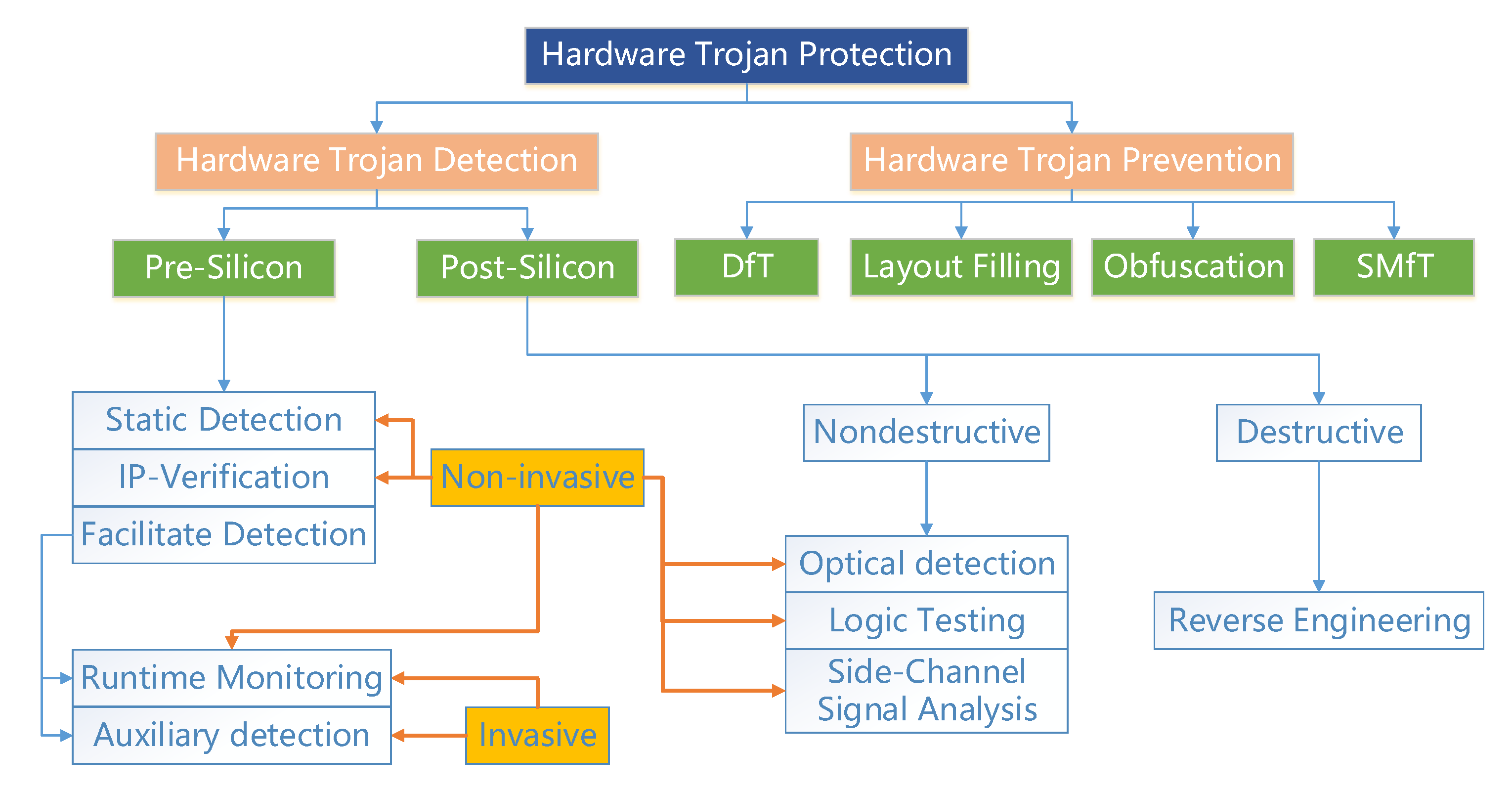
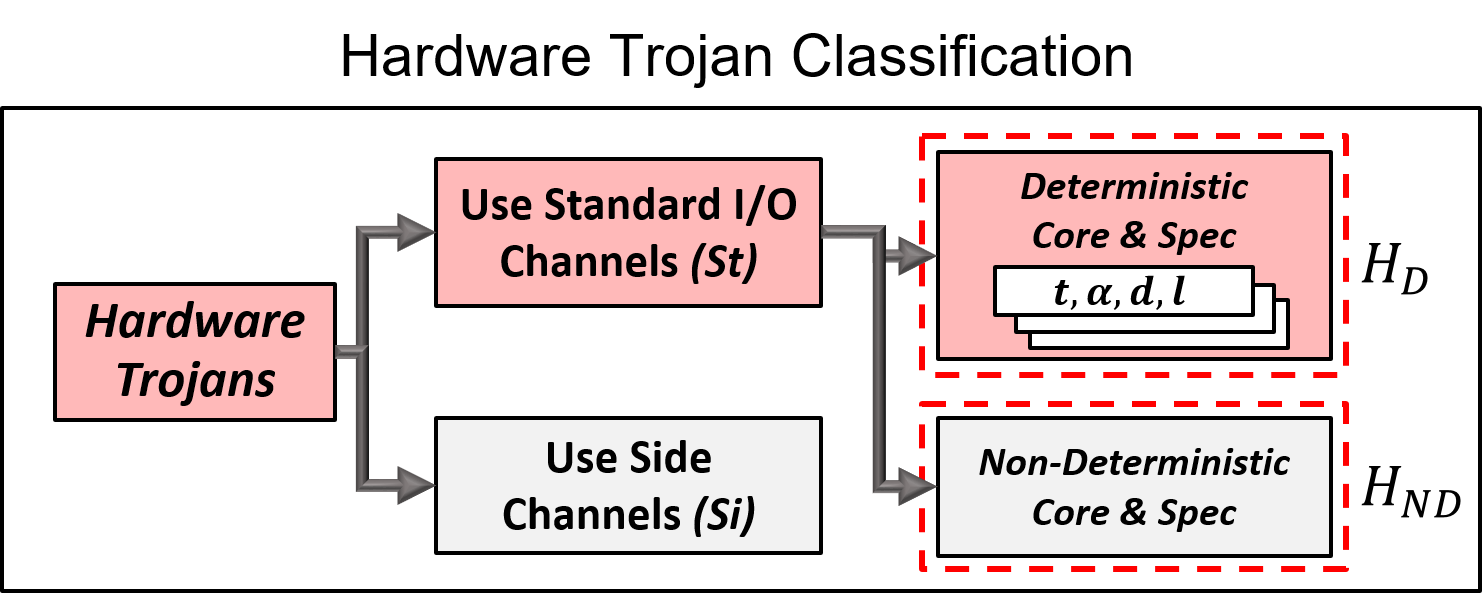
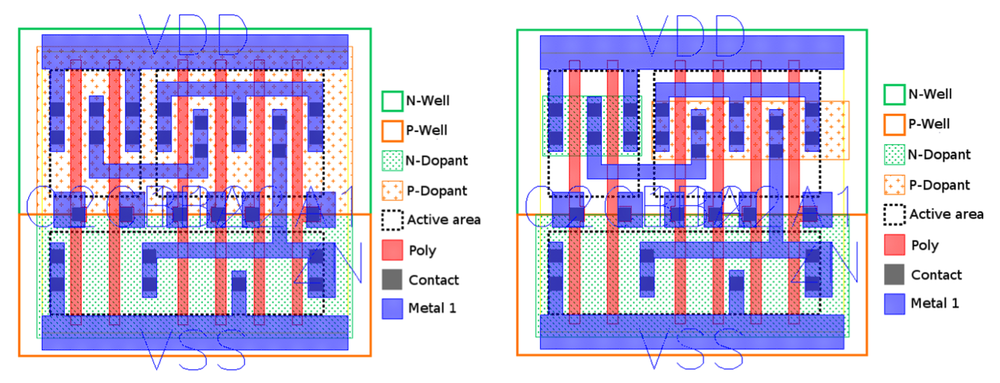
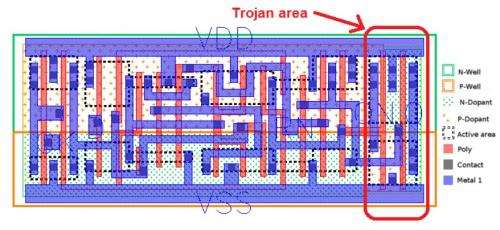
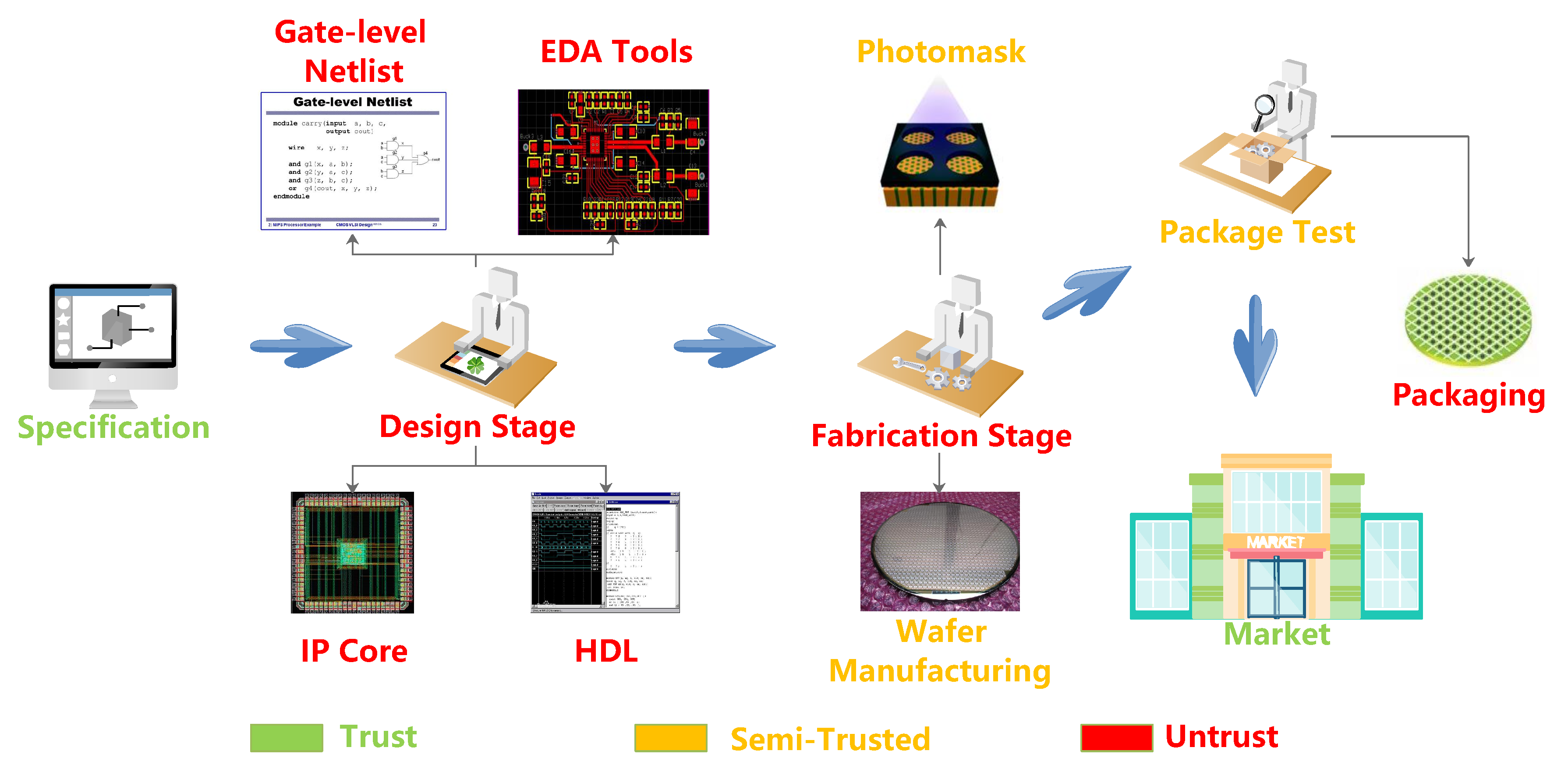
A Stealthy Hardware Trojan Exploiting the Architectural Vulnerability of Deep Learning Architectures · Issue #254 · BraneShop/showreel · GitHub
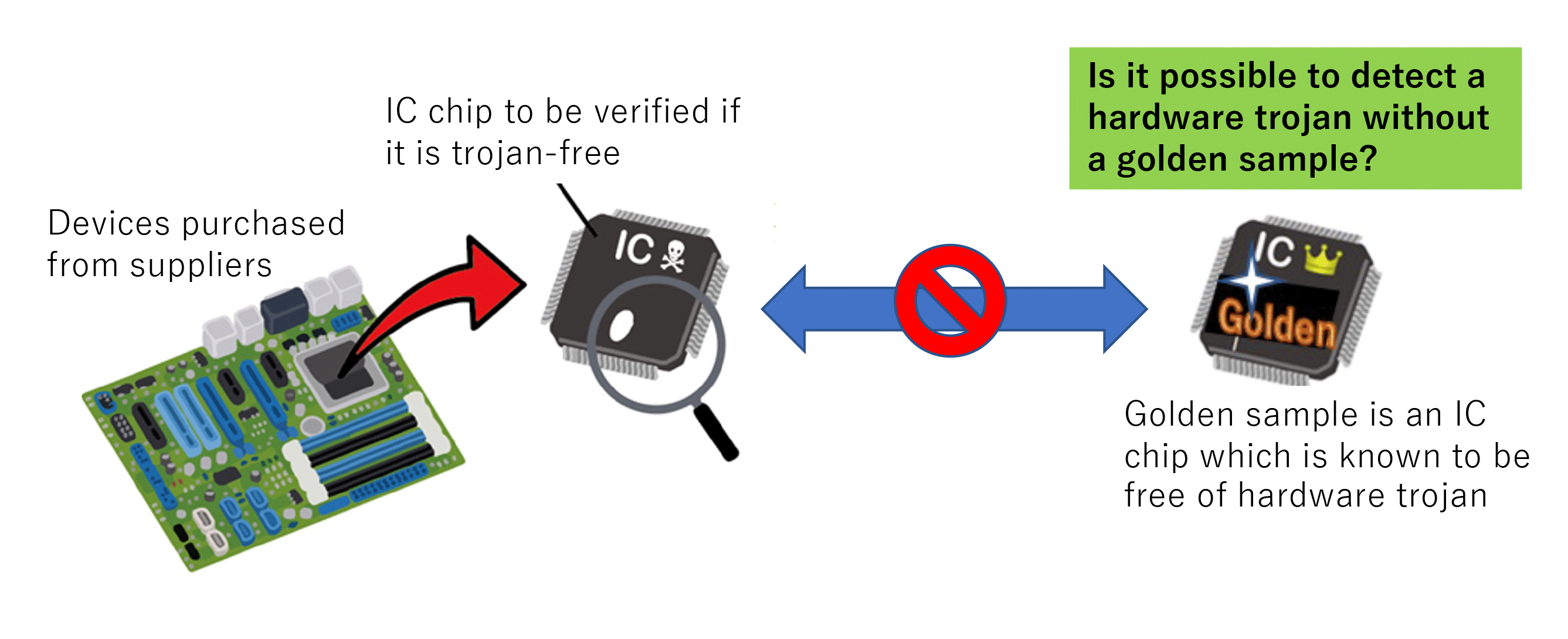
Research on hardware Trojan - Research | Hardware security research team | Cyber physical security reserch cente